Impersonation-as-a-Service: Characterizing the Emerging Criminal Infrastructure for User Impersonation at Scale
In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security (CCS 2020), 2020-11
Campobasso, M.; Allodi, L.
Mention in ACM CCS 2020 Highlights
PDF Datasets Conference Media coverage
Abstract
In this paper we provide evidence of an emerging criminal infrastructure enabling impersonation attacks at scale. Impersonation-as-a-Service (IMPaaS) allows attackers to systematically collect and enforce user profiles (consisting of user credentials, cookies, device and behavioural fingerprints, and other metadata) to circumvent risk-based authentication system and effectively bypass multi-factor authentication mechanisms. We present the ImpaaS model and evaluate its implementation by analysing the operation of a large, invite-only, Russian ImpaaS platform providing user profiles for more than 260'000 Internet users worldwide. Our findings suggest that the ImpaaS model is growing, and provides the mechanisms needed to systematically evade authentication controls across multiple platforms, while providing attackers with a reliable, up-to-date, and semi-automated environment enabling target selection and user impersonation against Internet users as scale.
Main research outcomes
We presented the IMPaaS model as a novel threat enabling attackers to perform user impersonation at scale. IMPaaS is supported by an emergent criminal infrastructure that control the supply chain of user profiles, from system infection to profile acquisition and commodification. Criminals produce fingerprints from compromised hosts, which are bundles of information containing credentials, cookies, history and behavioral metadata of the victim, allowing attackers to seamlessly reproduce a user's "appearance" in front of an authentication system. Such fingerprints are available on the IMPaaS platform for prices ranging from a few to hundreds of USD, depending on the wealth of the country of the victim, the amount of available accounts available and which accounts are contained. From our analysis, we identify a strong correlation in the price with the presence of credentials for banking websites, cryptocurrency exchanges and e-commerce accounts. In addition, our research provided further evidences supporting the claim that underground platform operators are actively monitoring crawling activities and take measures to limit them.
Appendix: Model derivation of an emerging threat from underground market observations
In this appendix, we detail the process we employed to derive each step of the IMPaaS criminal model. Whereas generally threat identification and derivation originate from technical observations of malicious activity (e.g., through malware reverse engineering, botnet sinkholing, etc.), in this paper we derived the IMPaaS threat model from observational data coming from the underground ecosystem itself. As criminal business models advance, being able to "reverse engineer" those to derive a bigger-picture view of the threat ecosystem has clear value: it allows us to better understand the criminal processes sustaining threat development and innovation, and provides us with insights on technical criminal artifacts we may have not yet detected "in the wild". In the following we share the process we followed to derive the IMPaaS model described in the paper, and synthesized below.
Data collection strategy
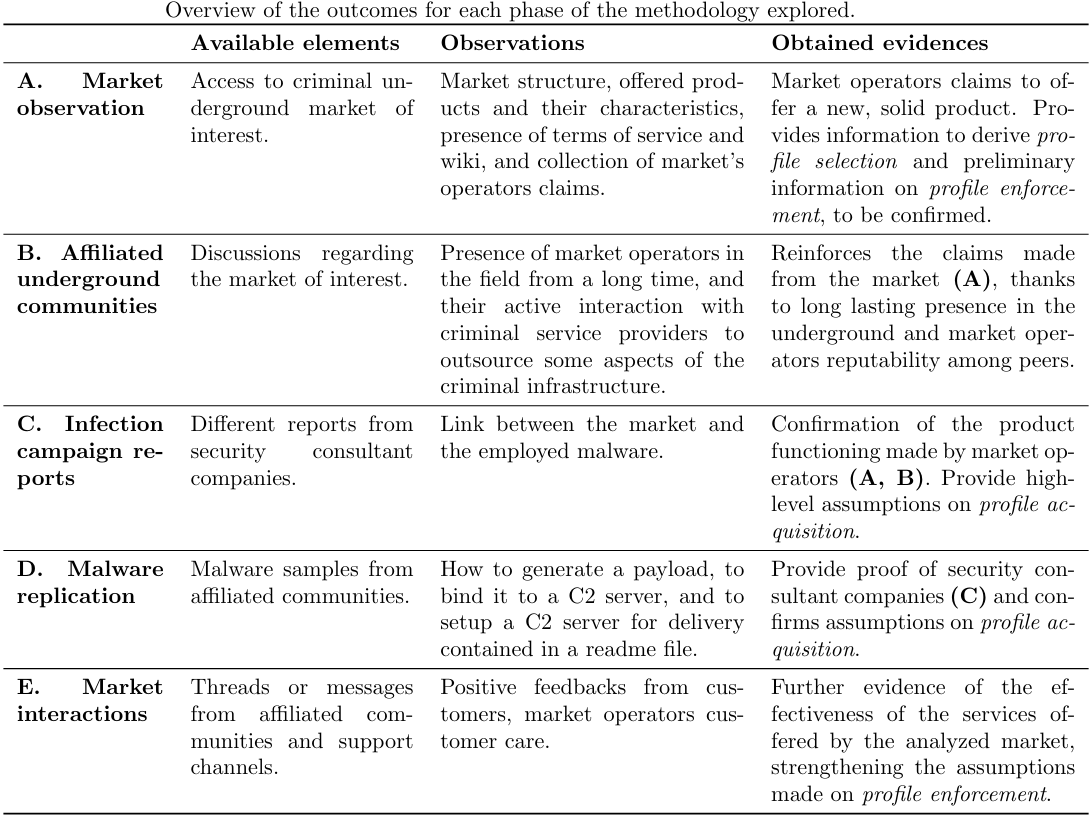
In the following, we describe how the model described in Figure 1 of the paper (reported below) has been derived from evidence collected following the strategy described above.
The Impersonation-as-a-Service Model
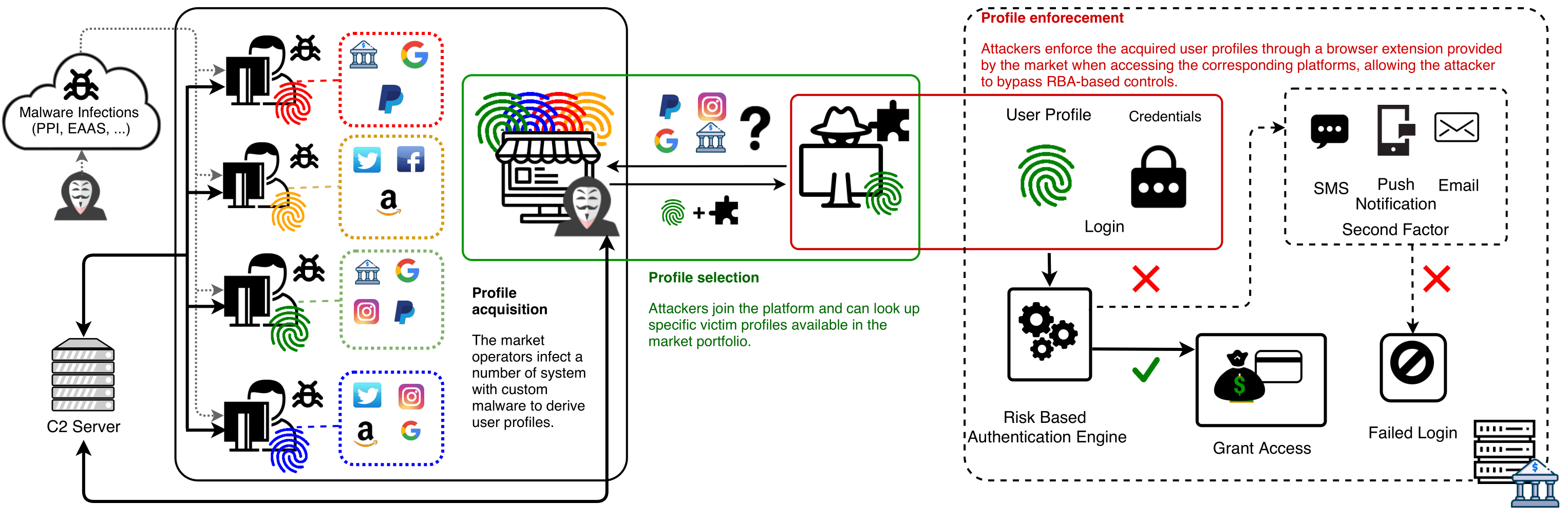
Profile acquisition
IMPaaS.ru offers hundreds of thousands user profiles where each of them, according to the marketplace's wiki, represents a single victim (A). As several security industry report from their investigations, to harvest this amount of user profiles, IMPaaS.ru was employing AZORult, an infostealer malware (C). To get a glimpse in the fuctioning of the malware, we collected several samples available on different underground communities in which we have a foothold; we consistently obtained a bundle containing a set of instructions, a payload generator and a C2 server. Then, we infected our test systems and observed the high-level functioning (D). In addition, in a post of a prominent underground marketplace, IMPaaS.ru operators were seeking for collaborators that could provide substantial quantities of infected hosts to control (B). The large amount of available user profiles on IMPaaS.ru and the IMPaaS.ru operators interactions on other prominent underground communities suggest that IMPaaS operators rely on large scale malware infections (provided by themselves, or from partnerships with PPI, EaaS, MaaS operators, or both), whose malware was AZORult (now dismissed), to fuel their market with user profiles.Profile selection
Once obtained access to IMPaaS.ru, the customer has access to the list of available user profiles (A). To better fit the needs of the customer, an advanced search tool allows to filter user profiles containing credentias for given websites, price range, country of infection, installation date and other parameters (A). After the first user profile is bought, the customer can download a custom version of Chromium and a plugin that will enforce the acquired user profile in the browser (A).Profile enforcement
The combination of user profile, browser and plugin empower the customer to an attacker capable of successfully impersonate the victim (A, B, E). From the market's wiki and from IMPaaS.ru operator's ads on affiliated communities, they claim that their solutions allow to reliably spoof the identity of a victim to the analytical systems employed from social and bank identity verification systems. (B). To achieve this, IMPaaS.ru operators claim that they collect a wide set of information from the victim's host, including the ones that major banks, payment and online antifraud systems monitor. Further, they claim that once an attacker enforces the fingerprint via the plugin, this information is provided to those systems. (B). From their claims, they're exploiting the ease of use introduced from usable security authentication mechanisms such as RBA to bypass potential second factor that may be triggered at login time. In addition, in the FAQ section of the market, they remark the importance of using unblacklisted and accurate SOCKS5 proxies to reproduce the geolocation of the victim (A). The plugin natively provides support to tunnel traffic into a user-defined SOCKS5 proxy, greatly improving the success rate of the impersonation attack (A). In addition to the economic considerations made in the paper regarding market's health, common only among established and serious underground markets, the market shows other signs of respectability. In fact, IMPaaS.ru operator's profiles in the affiliated (and sometimes prominent) communities have the status of "verified sellers" and come with a long message history (B). In these messages, they provide updates about evolutions of the marketplace and actively interact with customers, offering support and information (B, E). In these discussions, customers provide feedbacks to their peers about their experience; positive feedbacks are the majority. A minor portion of unsatisfied customers often complain about having bought a user profile that doesn't bypass 2FA or doesn't contain updated credentials (E). To these claims, the IMPaaS.ru operators respond that in their ToS they specify that user profiles are sold "as-is", with no warranties on their content and how to analyze them before buying (A, B). Nonetheless, IMPaaS.ru operators show their efforts in improving the quality of the service; to this extent, they implemented a feedback system for user profiles to better understand which profiles meet the quality required from customers (A, E). To further incentivize customers in using it, they offer a 5% cashback on the value of the reviewed profile (A, E). Finally, some Telegram channels created by IMPaaS.ru operators offer customers the chance to share their experiences and offer their techniques to cashing out victim's assets, often upon payment (E).Conclusions
From these observations, we derive Impersonation-as-a-Service as an emerging threat model to established authentication mechanisms. Albeit we didn't had on hand any user profile due to ethical concerns, the observable criminal ecosystem around this market offers convicing evidences that the IMPaaS model is emerging and can lead arbitrary attackers to successfully impersonate victims at scale. IMPaaS.ru clearly identifies strengths and limitations of the offered solution. Nonetheless, we believe that the existence of IMPaaS.ru, their business model and their presence on the market indicate a strong interest from customers and a proved being able to support impersonation attacks at scale, offering the needed driving force for other and more sophisticated IMPaaS providers to appear in the cybercriminal panorama.Media coverage
[] ACM CCS - CCS 2020 Highlights - Latest In Cybersecurity Research Unveiled at ACM Conference on Computer and Communications Security[] Troy Hunt: Seized Genesis Market Data is Now Searchable in Have I Been Pwned, Courtesy of the FBI and "Operation Cookie Monster"
[] TU/e - Researchers TU/e find huge and sophisticated black market for trade in online ‘fingerprints’
[] InnovationOrigins.com - Large-scale criminal online market in user profiles
[] TechXplore.com - Researchers find huge, sophisticated black market for trade in online fingerprints
[] TU/e - Onderzoekers TU/e vinden enorme zwarte markt voor handel in online ‘fingerprints’
[] Computer Idee - Uitsmijter - Illegale handel in online ‘fingerprints’
[] NPO Radio 1 - Radio EenVandaag
[] NPO Radio 1 - Radio EenVandaag (web) - Waarom cybercriminelen nu zelfs uit zijn op hoe snel je typt, je beeldschermgrootte en muisbewegingen
[] Radio 538
[] QMusic
[] Eindhovens Dagblad - Russen handelen op ‘marktplaats’ in gestolen online identiteiten, ontdekten Eindhovense onderzoekers
[] Eindhovens Dagblad - Onderzoekers TU/e vinden illegale Russische marktplaats voor online profielen
[] Tweakers.net - Onderzoekers vinden website die 'fingerprints-as-a-service' aanbiedt
[] De Volkskrant Tech - Data duizenden Nederlanders op Russisch forum (bottom of page)
[] Volkskrant Tech - Gegevens van duizenden Nederlanders verhandeld op marktplaats
[] Fontys.nl - Omvangrijke criminele online handel in gebruikersprofielen
[] RTL Nieuws - Data duizenden Nederlanders verhandeld op criminele marktplaats
[] Reformatorisch Dagblad - Gegevens van duizenden Nederlanders verhandeld op marktplaats
[] Studio 040 - TU/e legt Russische handel in digitale 'fingerprints' bloot
[] Nederlands Dagblad - Gegevens van duizenden Nederlanders verhandeld op marktplaats
[] Technisch Weekblad - Onderzoekers TU/e vinden enorme zwarte markt in online ‘fingerprints’
[] Computable - Marktplaats nog geen techparadijs voor cybercrimineel
[] Trouw - TU Eindhoven spoort handel op in online vingerafdrukken
[] Hart van Nederland - TU Eindhoven ontdekt Russische website voor handel in online vingerafdrukken
[] RTL - 'Site met handel in profielen biedt toegang tot 260.000 accounts'
[] Brabants Dagblad - Onderzoekers TU/e vinden illegale Russische marktplaats voor online profielen"
[] agConnect - Online-fingerprinthandel blootgelegd door TU Eindhoven
[] VPNGids - TU Eindhoven stuit op zwarte markt voor digitale fingerprints
[] ICT/magazine - TU/e ontdekt enorme zwarte markt voor handel in online fingerprints
[] Security NL - Marktplaats voor gestolen profielgegevens laat criminelen RBA-systemen omzeilen
